Solutions

Sharetech: OT Security Solutions
Intel Market Ready SolutionDescription
OT Security Solutions
The Security Solution Dedicated to Industrial System
For most people, the internet is a virtual concept. We could barely be aware of its value. However, in those ages that the internet had not been invented, letters were the essential material for communicating. Along with the development of the internet, no matter when and where we are, messages can be sent instantly. Nowadays, with communication software like LINE, WhatsApp, and Skype, the physical distance is no longer a problem.
IT Mindset vs. OT Mindset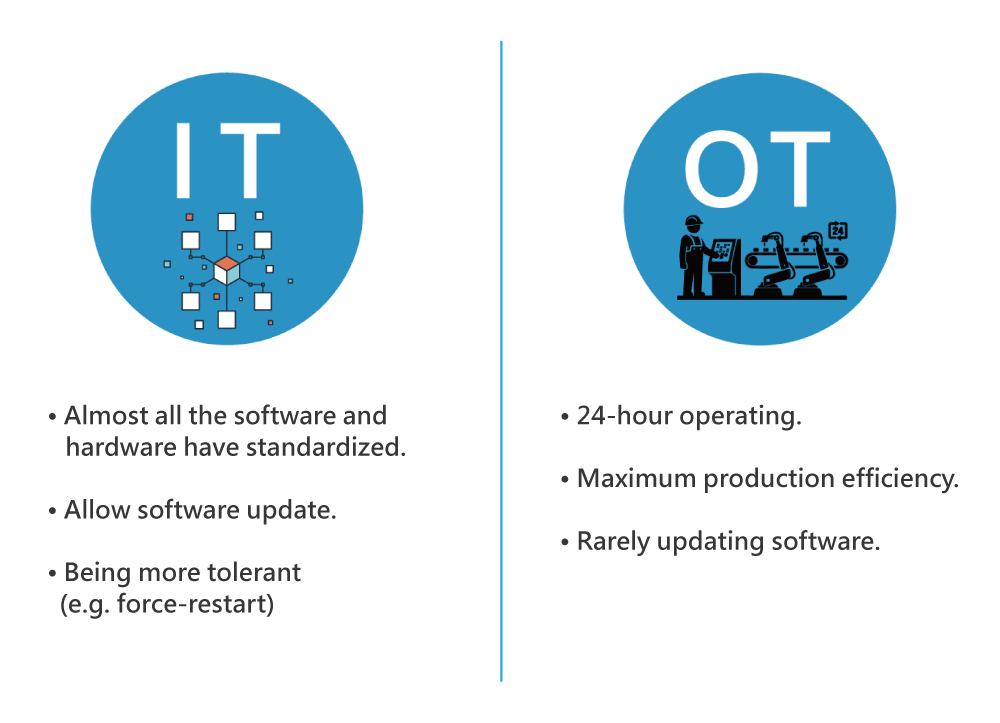
The potential risk of OT environment
When the industrial plans to introduce IIoT, network security is the crucial point. For more than 20 years, ShareTech dedicates to providing user-friendly and secure products. We find out that many factories exist three high risks: risk of network connection, remote access, and terminal device usage. Therefore, ShareTech OT security solution provides full functions product to secure the OT environment, e.g., remote access control, authentication, OPC intrusion prevention.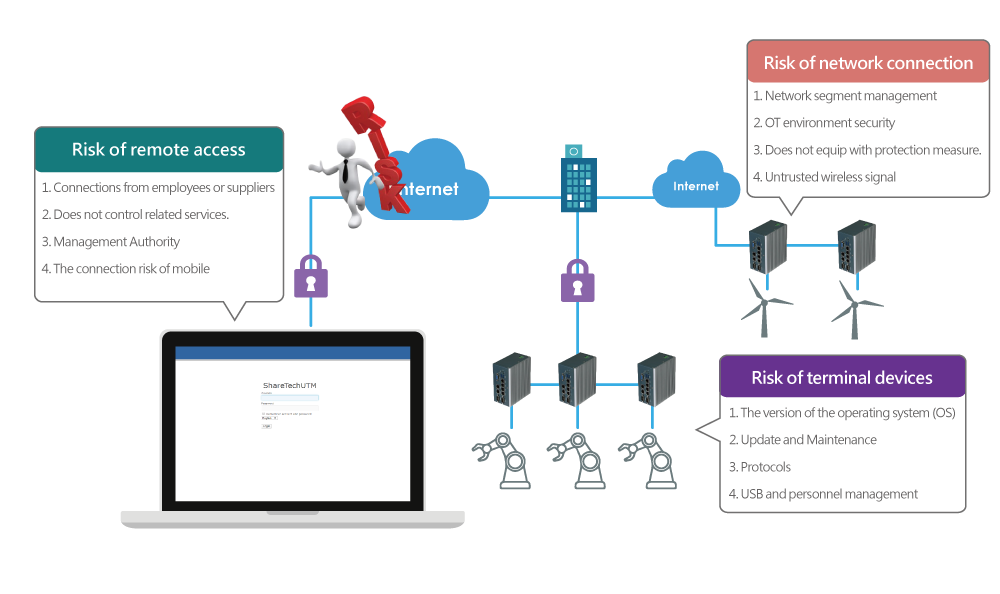
IoT Solution Application
ShareTech OT Security Solution
- High-level hardware design
To secure connections, ShareTech OT security products support interfaces like Ethernet, WiFi, 3G/4G, serial port (RS232/RS485), and DI/DO. Besides, they are OT hardware formats that support din-rail, terminal block power supply, and wide temperature.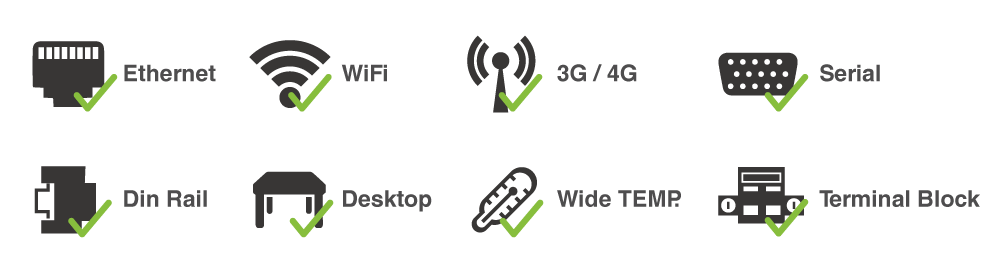
- Enhance OT network traffic inspection
ShareTech OT security products can detect malicious traffic, for example, illegal remote access, malware infection of PC. With monitoring, detecting, and acting, ShareTech OT security products collect packets and signals from both IT and OT networks. Use DPI technology to analyze abnormal packets and decrease these incidents that can let hackers easily enter production lines.
- Boundary defense
Industrial boundary defense appliances include industrial firewall, industrial gateway, unidirectional network device, etc. Every enterprise should deploy boundary defense appliances in each border. ShareTech suggests separate IT and OT environments avoid cluster infection when hackers invading.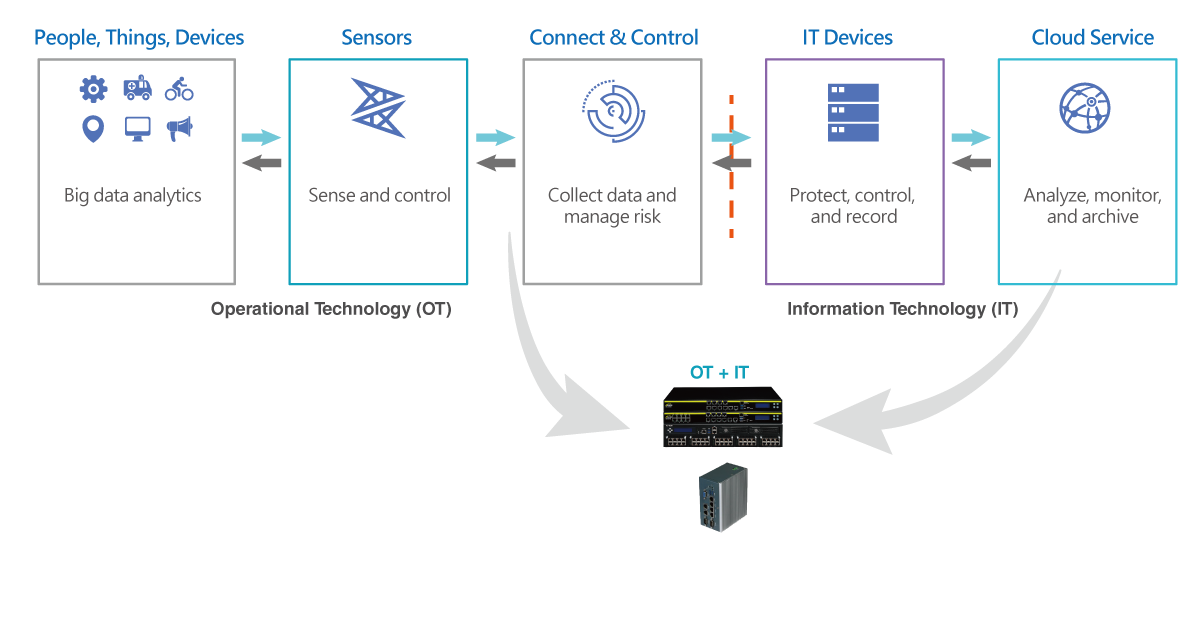
- Raise the visibility of cyberthreats
- Disclose the hidden threats
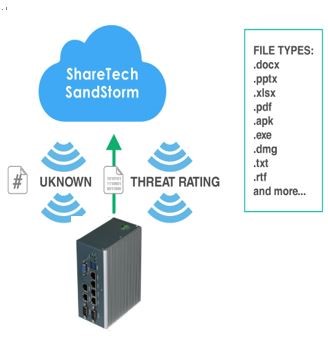
Enhance the visibility of high-risk activity, suspicious traffic, and advanced threat. - Prevent Unknown Threat
Protect the network through big data analysis, big data learning, and virtual patch. - Quarantine Infected System
Automatically quarantine the hacked system to prevent spreading out.
- Remote access security
With more external ports means raising the exposure risk. Rather than using port connection, IPSec VPN is the best way to build a secure VPN connection, no matter using dynamic IP or static one.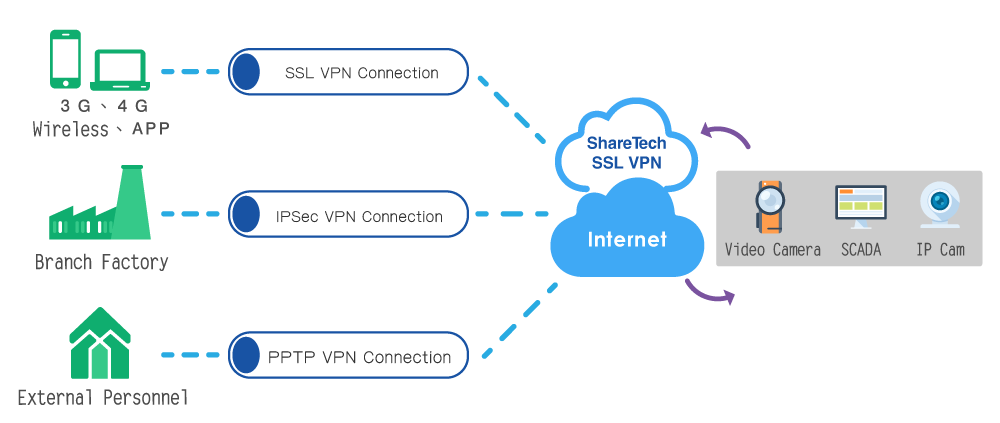
- Multiple layers of defense
Administrators seldom notice the anomaly of devices or the penetration of hackers if the devices can operate normally. This makes hackers easy to attack. In the IT environment, people usually let all the traffic in and block specific services only. However, in the OT environment, allowlist should be implied. Only those applications and services that are on the list can operate to protect those OT appliances actively.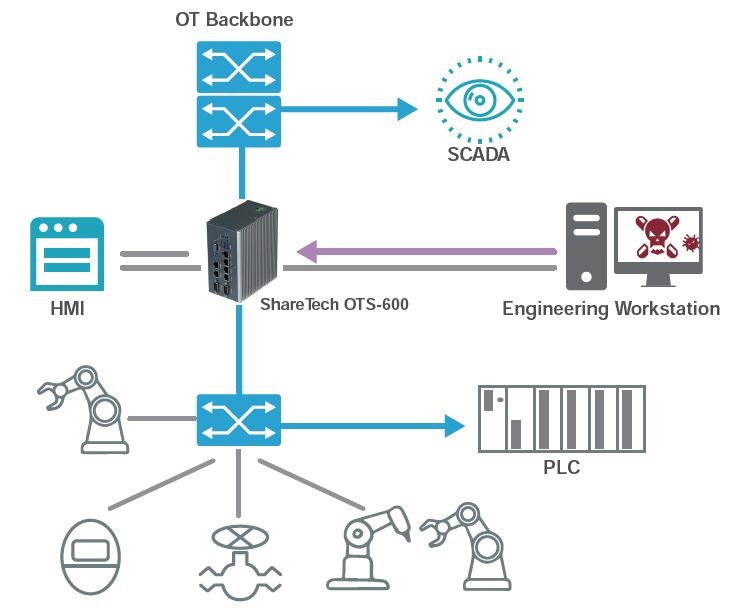
- OPC intrusion prevention
Collect all the packets from both IT and OT networks and use deep packet inspection (DPI) technology to verify and analyze. According to these abnormal traffics, ShareTech OT security device will generate related logs. Through these logs, administrators can easily make all the information of the events under control and can follow up afterward.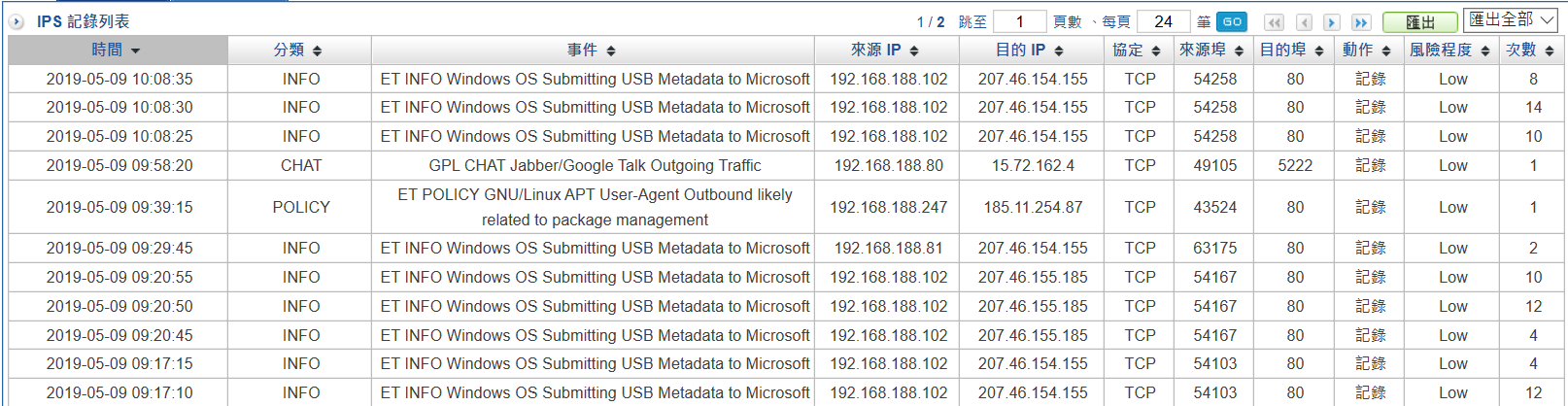
- Virtual Patch Protection
To avoid zero-day attack, ShareTech OT security device equips with virtual patch function. When your devices are out of maintenance and exist lots of vulnerabilities, Virtual Patch will help you block all the threats.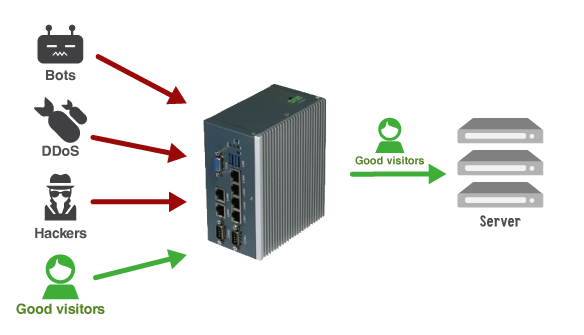
- Big data analytics—Dashboard
From the data of both IT and OT devices, ShareTech OT security device analyzes and generates a dashboard. This can help administrators easily understand the network security condition of the factory. If a cybersecurity incident happens, the dashboard will demonstrate the process and results. Besides, the dashboard will also show the operating situation of the devices and make the potential risk stand out.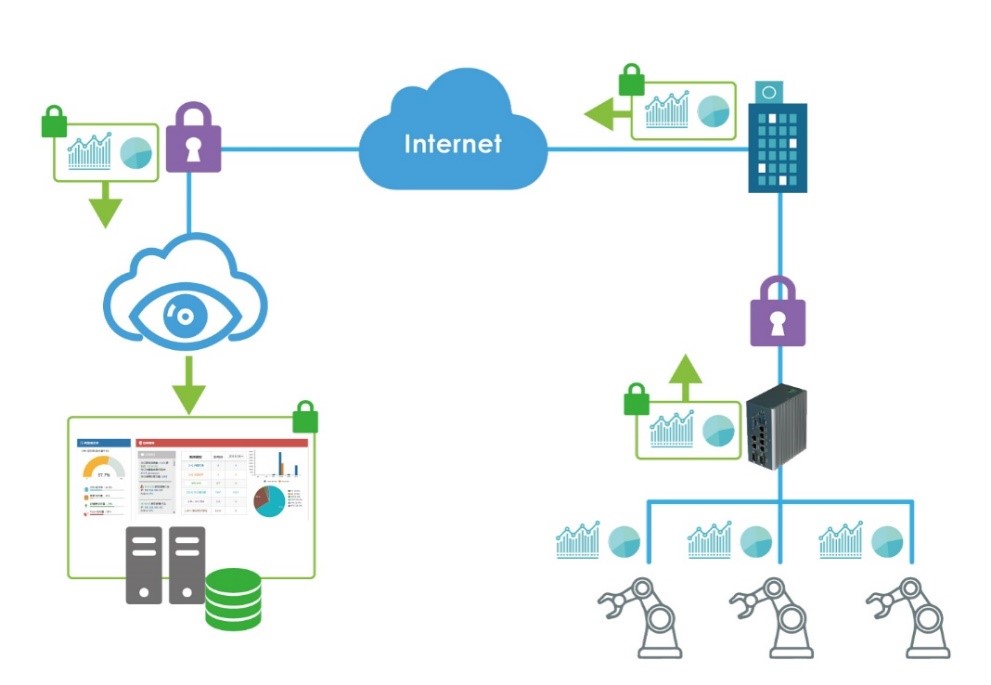
- OT Cloud Management Platform: rapid deployment, simple management, and easy maintenance
Even encounter complicated OT networks, with one single platform, ShareTech Cloud Management Platform makes network management easier.
What makes ShareTech Cloud Management Platform different?
- Fully present operating status of OT devices.
- Support industrial protocols.
- Provide real-time monitor and instant alarm notification.
- Backup and restore configuration.
- Support USB instant recovery.
- Support central management system (CMS).
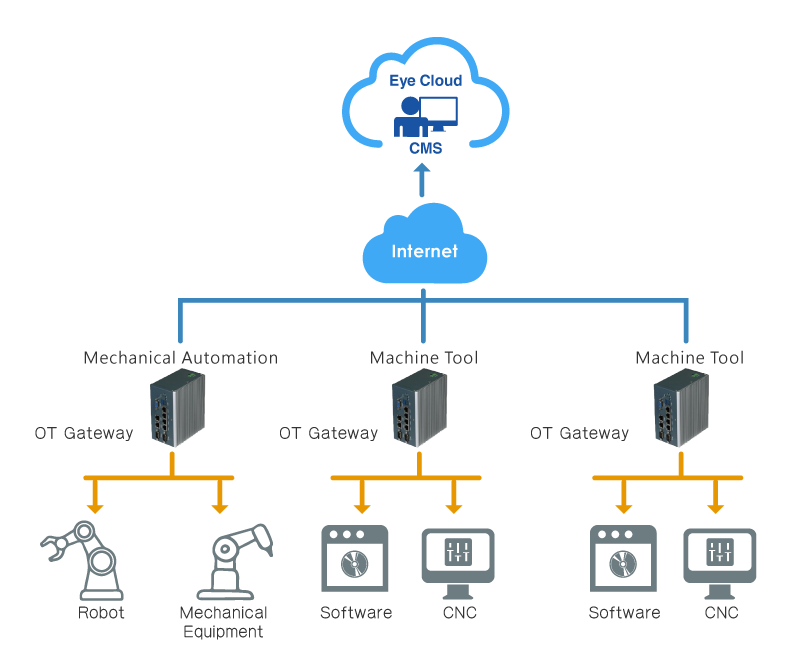
Application Environments
- Manufactories
With many devices deploy around the world, industrial 4.0 is a big challenge for manufactories.
- Intelligent plant (ICS & medical care institutions)
The intelligent plant brings chances and benefits, but it also brings risks and threats. To obtain security and efficiency, measures preventing cyberthreats are also essential.
- Critical Infrastructure (water, electricity, and power source)
The protection of critical infrastructure can assure not only economic security but the life safety of its staff members. It is convenient using remote access and monitor. However, enhance security is also crucial.
IoT Solution Specification
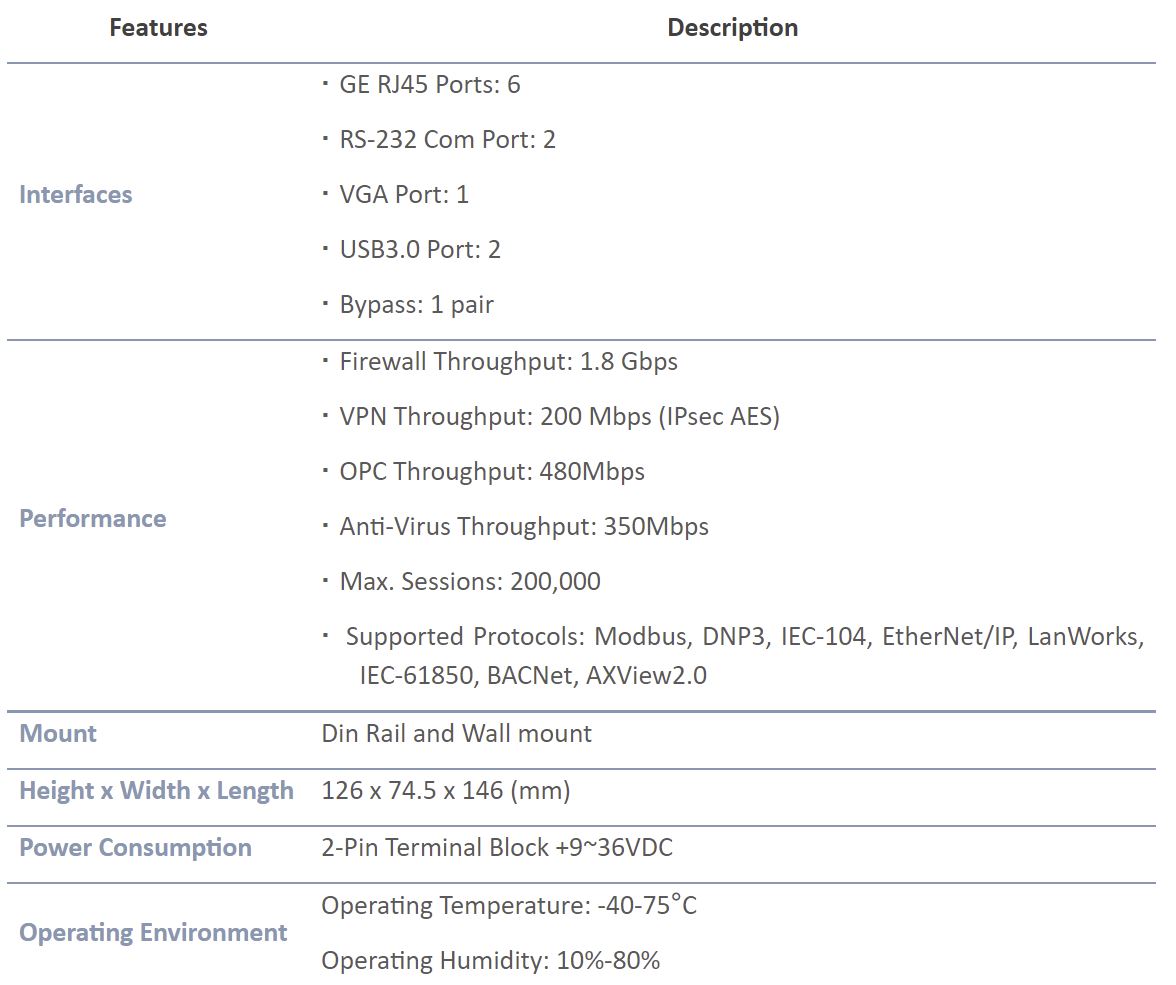
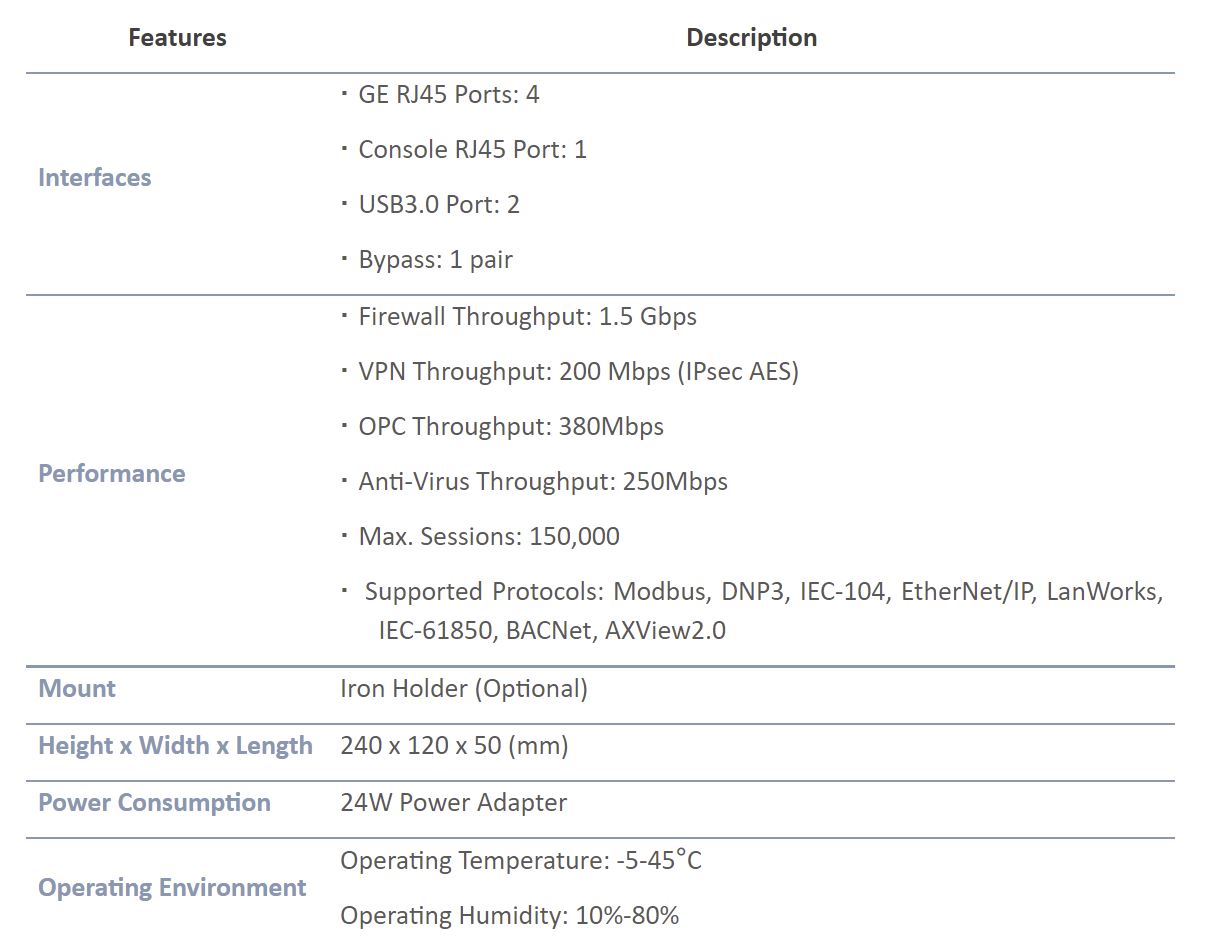
OTS SeriesOTS-400
- Interfaces: 4xGbE RJ-45
- Firewall Throughput: 1.5 Gbps
- OPC Protection: 380Mbps
- Max. Sessions: 150,000

OTS-600
- Interfaces: 6xGbE RJ-45
- Firewall Throughput: 1.8 Gbps
- OPC Protection: 480Mbps
- Max. Sessions: 200,000